SERVICES
Home SERVICES
Which solution is right for you?
We offer a variety of services tailored to Fit your individual needs.
EXTENDED DETECTION & RESPONSE (XDR)
H&A seeks to establish a partnership to deliver our Extended Detection and Response (XDR) solution, encompassing advanced cybersecurity capabilities. Our XDR solution offers comprehensive visibility and protection across an organization’s entire IT environment, enhancing their security posture.
XDR integrates and correlates data from various security technologies and sources, including managed detection and response (MDR), network security monitoring (NSM), security information and event management (SIEM), managed security operations center (MSOC), cloud monitoring, and other essential security tools. This consolidation of data provides a unified view of an organization’s security landscape, enabling more efficient threat detection and response.

XDR Services
MANAGED SECURITY OPERATIONS CENTER (MSOC)
The Managed Security Operation Center (MSOC) is a cybersecurity service designed to ensure round-the-clock protection for your organization. This service harmonizes the power of cutting-edge technology with deep human expertise, providing comprehensive surveillance, detection, analysis, and response to all types of cyber threats.
Our MSOC services leverage a state-of-the-art Security Information and Event Management (SIEM) platform, advanced threat intelligence, and a dedicated team of cybersecurity experts working 24/7 to safeguard your digital assets. We don’t just detect threats; we analyze them in real time, guide your response actions, and help remediate issues, ensuring your organization’s resilience in the face of an evolving cyber threat landscape.
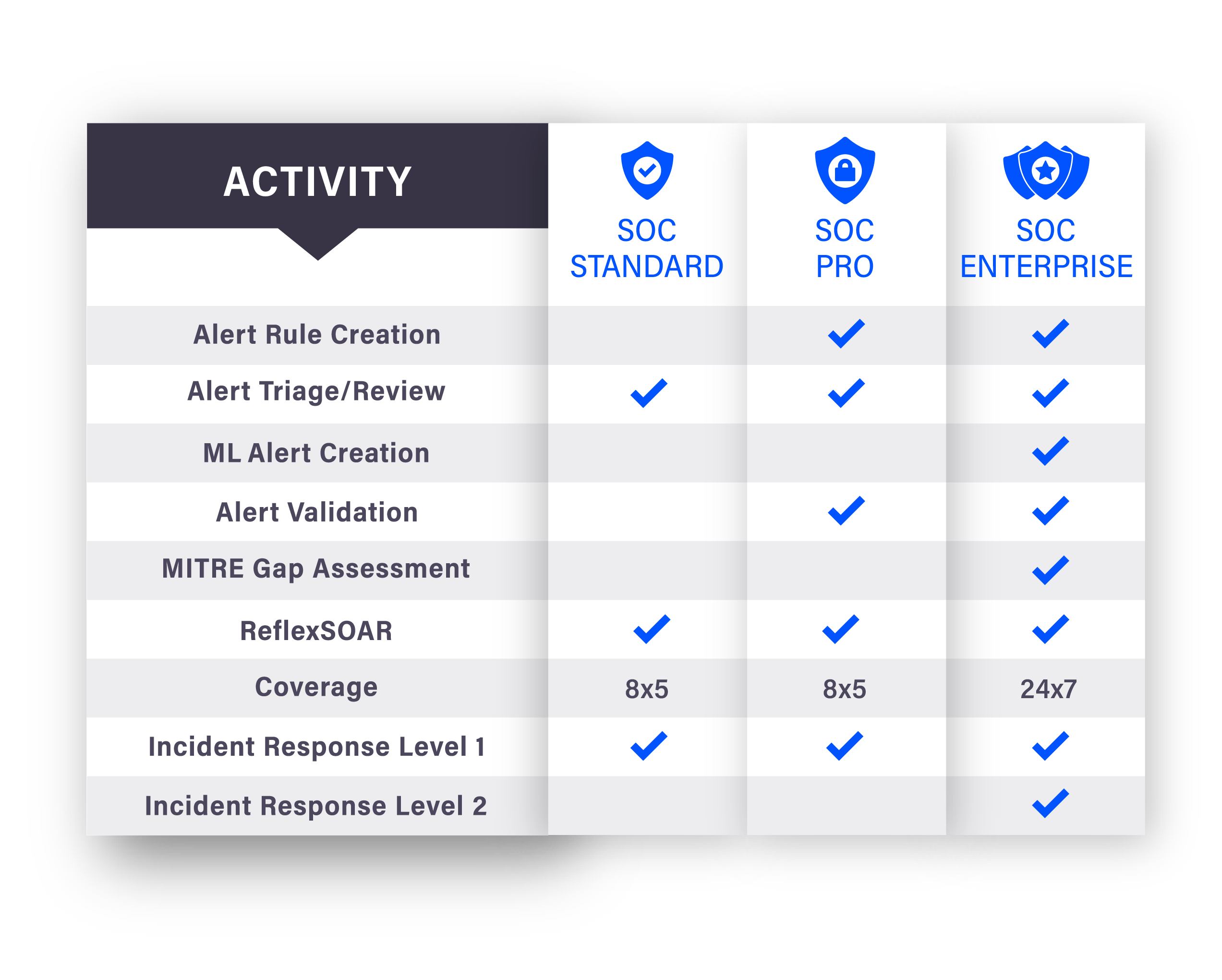
MSOC Services
MANAGED DETECTION & RESPONSE (MDR)
Our Managed Detection and Response (MDR) Service is a comprehensive cybersecurity solution, combining advanced technology with human expertise to continuously monitor, detect, investigate, and respond to cyber threats in your organization’s digital environment.
Using a suite of advanced tools including AI and machine learning, our MDR service is designed to detect both known and unknown threats, including complex, stealthy attacks that traditional security measures might miss.
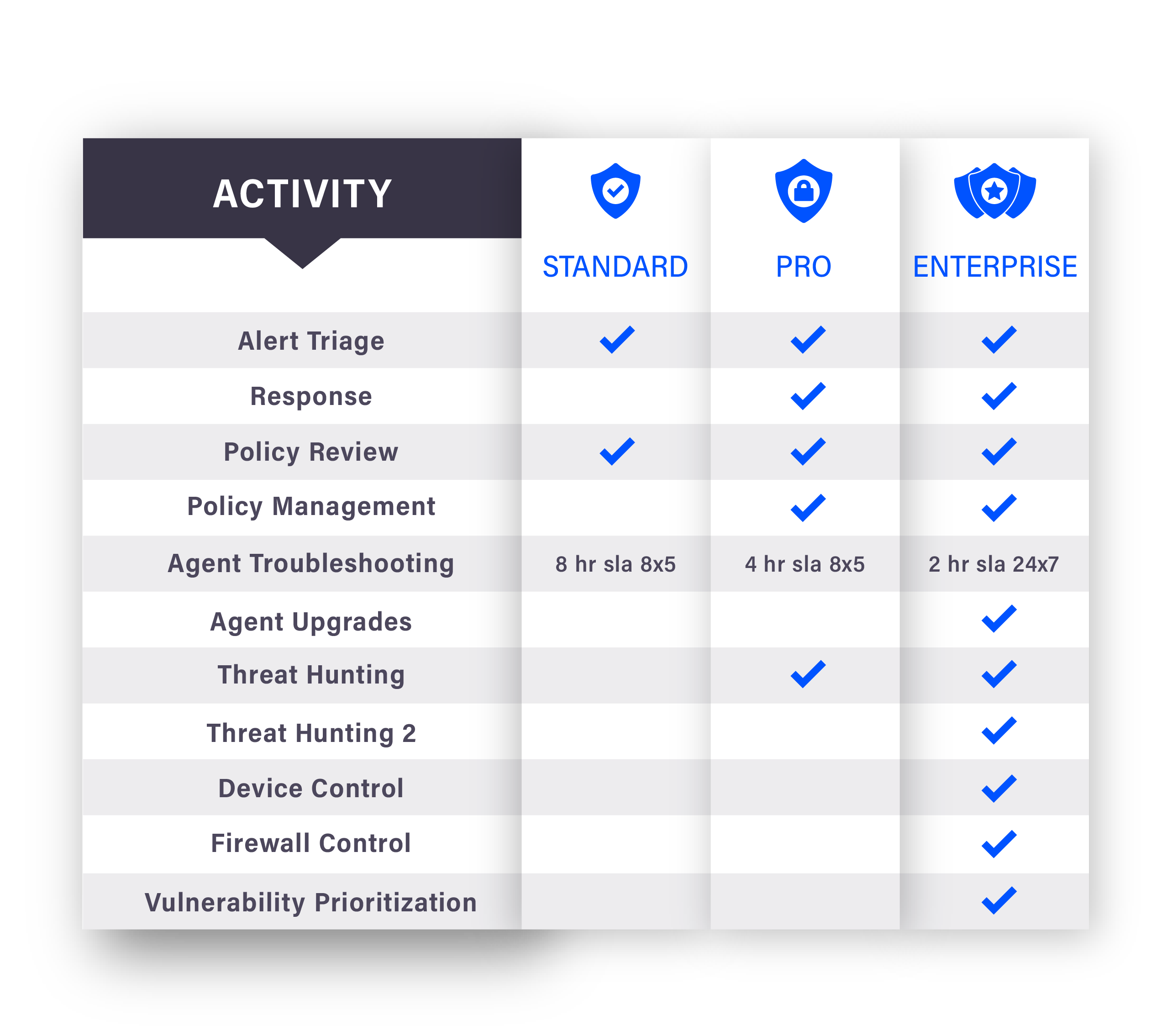
MDR Services
SECURITY INFORMATION & EVENT Management (Siem)
Our Security Information and Event Management (SIEM) Service is a robust cybersecurity solution that fuses advanced technology with human expertise to provide real-time analysis of security alerts generated across your organization’s environment.
Designed to give organizations a higher degree of visibility over their digital environments, our SIEM service combines the power of log management, event correlation, and security analytics. This allows for efficient threat detection, detailed incident investigations, rapid response times, and enhanced regulatory compliance.
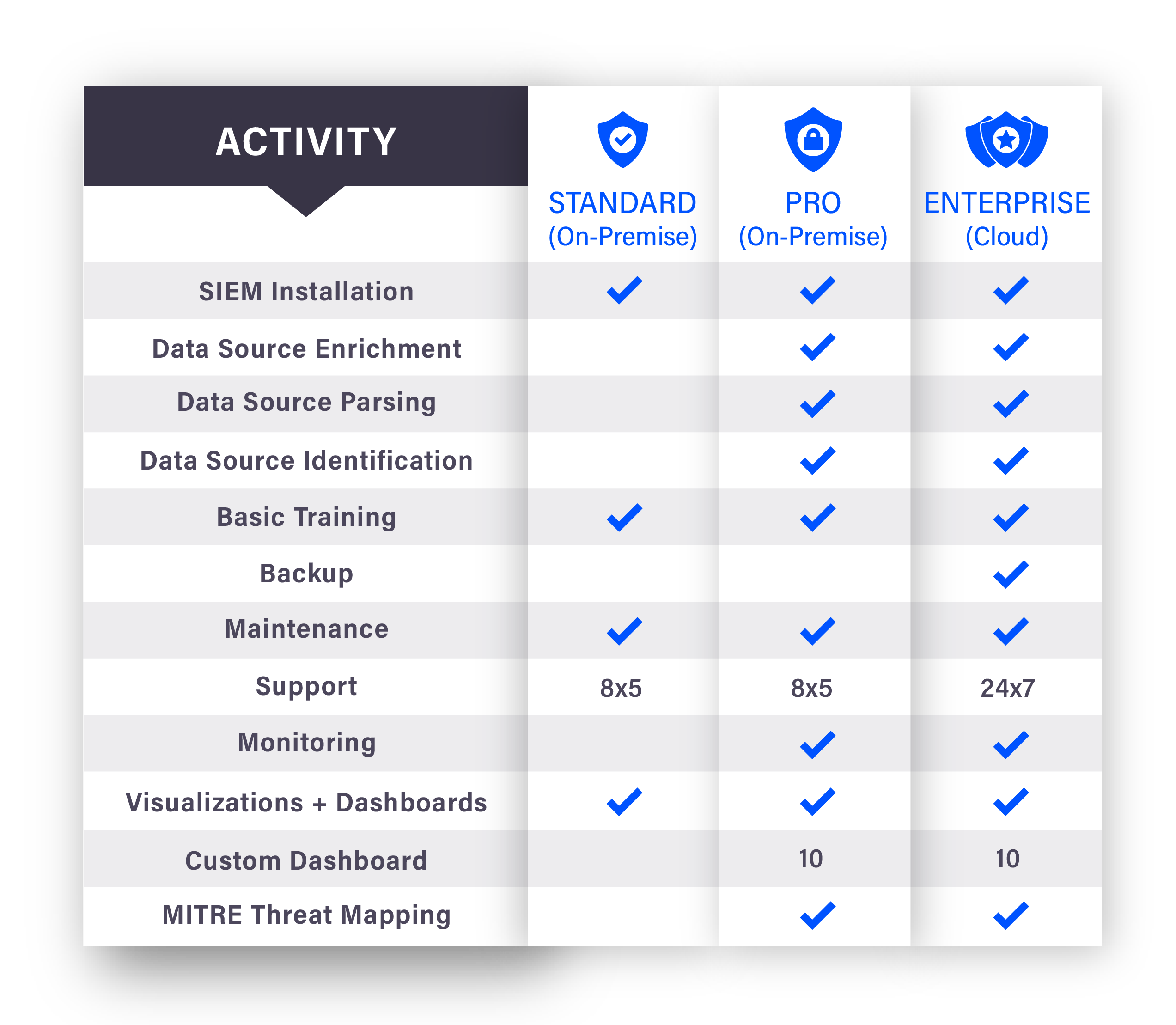
SIEM Services
Vulnerability management (vm)
Our Vulnerability Management Service is a comprehensive cybersecurity solution designed to identify, classify, prioritize, and remediate potential weaknesses in your digital infrastructure. This proactive service ensures the integrity of your systems, safeguarding them against ever-evolving cyber threats. By utilizing state-of-the-art scanning technologies and threat intelligence, we effectively uncover and evaluate vulnerabilities in your network, applications, and systems. Our team of cybersecurity experts then prioritizes these vulnerabilities based on their potential impact and the threat landscape, providing a roadmap for targeted and effective remediation actions.
In addition, our service includes regular vulnerability reporting, providing you with clear insights into your security posture and compliance status. With our Vulnerability Management Service, organizations can bolster their defense mechanisms, mitigate risk, and maintain the trust of their stakeholders by demonstrating a robust approach to cybersecurity.
vm Services
FOR MORE IN DEPTH INFORMATION ON ANY OF OUR SERVICE OFFERINGS CHECK OUT OUR DIGIZINE
Our goal is to be your strategic partner, leveraging our fifteen years of experience in the cybersecurity field to continually improve our service offerings and deliver tangible value.